The hacker behind the $9.6 million exploit of decentralized lending platform zkLend in February 2025 has reportedly been targeted by a phishing scam, resulting in the loss of more than half of the stolen funds.
According to a message sent on March 31st via Etherscan, the attacker claimed they mistakenly used a fake front-end impersonating Tornado Cash, a popular Ethereum-based privacy tool, and lost 2,930 Ether (worth roughly $5.4 million) in the process.
“Hello, I tried to move funds to a Tornado, but I used a phishing website, and all the funds have been lost. I am devastated. I am terribly sorry for all the havoc and losses caused,” the hacker wrote.
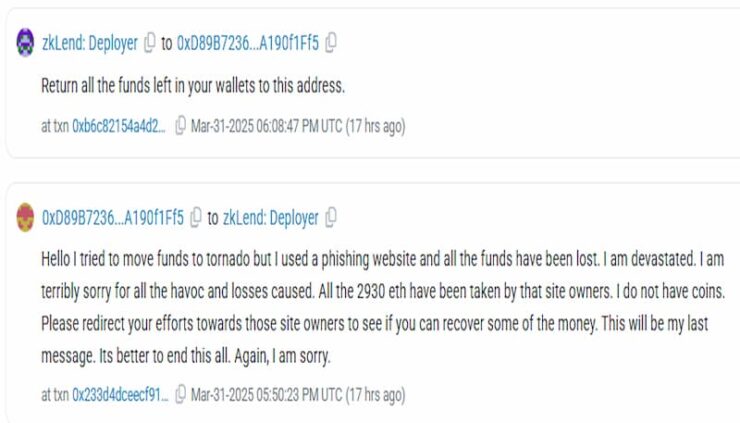
“All the 2,930 ETH have been taken by that site owners. I do not have coins. Please redirect your efforts towards those site owners to see if you can recover some of the money,” they added.
Blockchain data shows the hacker had been transferring 100 ETH at a time to a contract labeled “Tornado.Cash: Router,” finishing with three 10 ETH transactions—all of which were directed to the phishing site’s address.
An onchain observer even attempted to warn the attacker before the full amount was drained:
“Zklend hacker don’t celebrate,” the user said, referencing the fact that the funds had been routed to a scam version of Tornado Cash.
“It is so devastating. Everything gone with one wrong website,” the hacker responded.
The stolen ETH is now presumed lost unless law enforcement or security firms can track down the operators of the fake website.
In response to the hacker’s message, zkLend urged the attacker to return any remaining funds:
“Return all the funds left in your wallets,” the team wrote, providing a wallet address.
However, moments later, the exploiter transferred another 25 ETH to an unrelated wallet labeled Chainflip1, according to Etherscan.
How zkLend Was Exploited
The original attack occurred on February 12, exploiting a vulnerability known as an “empty market exploit.” According to a February 14th post-mortem, the attacker used a combination of flash loans and small deposits to inflate the protocol’s lending accumulator, then leveraged rounding errors to withdraw far more than deposited.
After bridging the stolen funds to Ethereum, the attacker initially tried to launder them through Railgun—but failed due to a protocol feature that redirected the funds back to the original address.
In an attempt to recover the ETH, zkLend publicly offered the hacker 10% of the funds as a white-hat bounty, with a promise of no legal action if the remainder was returned by Feb. 14. The deadline came and went with no response.
By Feb. 19, zkLend shifted its strategy, offering a $500,000 reward for verifiable information leading to the hacker’s identity and recovery of the funds.
The zkLend phishing twist adds a surprising footnote to another active month of crypto hacks and scams. According to CertiK, losses in March totaled $33 million, though that figure dropped to $28 million after 1inch successfully recovered stolen assets from a separate incident.
But February’s figures were far more alarming. Crypto-related losses soared to $1.53 billion, driven almost entirely by the $1.4 billion Bybit hack attributed to North Korea’s Lazarus Group, now the largest crypto exploit on record, surpassing the $650 million Ronin bridge hack in 2022.
A Stark Reminder of DeFi’s Fragility
The zkLend incident now reads like a cautionary tale—not just for DeFi protocols, but for the hackers targeting them. While the attack caused serious financial damage to users, the attacker’s downfall underscores a deeper truth about the crypto landscape: even those who exploit the system are not immune to its risks.
As zkLend and security teams continue investigating, one thing is clear, karma on the blockchain is brutally efficient.





