A new crypto job scam is draining victims’ wallets, using fake offers and malware-infected apps like GrassCall to exploit job seekers.
A sophisticated social engineering scam has been uncovered, where cybercriminals use fake job offers and a malware-laden app called GrassCall to infect victims’ devices and drain their crypto wallets.
According to a Feb. 26 report by BleepingComputer, the actors behind the scam have now abandoned the scheme, as LinkedIn accounts, fake job listings, and scam websites tied to the operation have been taken down. However, hundreds of people were reportedly targeted, with some victims confirming their crypto wallets were raided after downloading GrassCall.
Cybercrime Group ‘Crazy Evil’ Identified as Mastermind
The Russia-based cybercrime group ‘Crazy Evil’ is believed to be behind this latest fraud. The group specializes in targeting crypto users, utilizing spearphishing tactics to infiltrate victims’ devices.
Cybersecurity firm Recorded Future reported in January that it linked more than ten active scams to Crazy Evil, all of which were aimed at stealing cryptocurrency. One of these scams, Gatherum, appears to be a precursor to GrassCall, using the same branding, logo, and strategy.
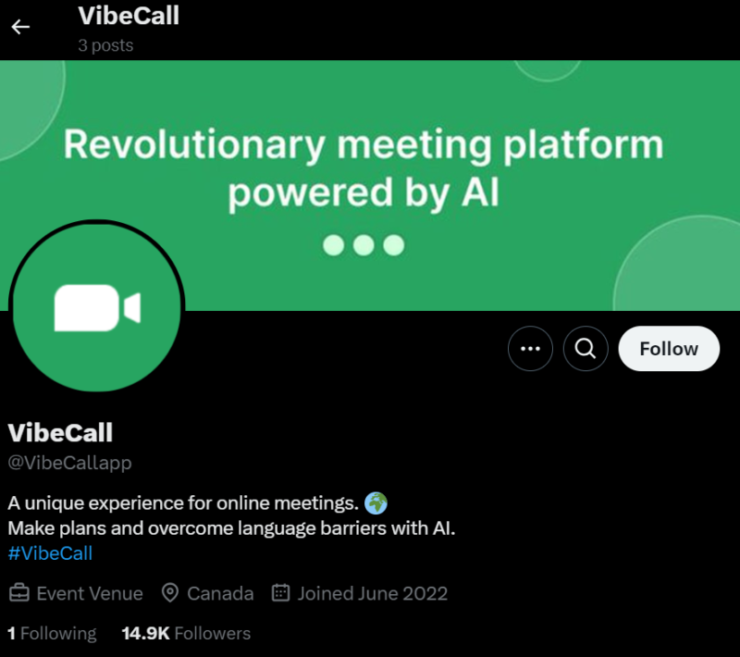
An X account named ‘VibeCall’, carrying the same logo as Gatherum and GrassCall, also surfaced in mid-February, despite its creation date of June 2022.
Fake Company ‘Chain Seeker’ Used to Recruit Victims
The fraudulent job scam revolved around a fake crypto firm called ‘Chain Seeker’, which set up social media accounts to create job listings on platforms such as LinkedIn, CryptoJobsList, and WellFound.
Applicants who responded to these job listings were contacted via email and directed to a fake ‘marketing chief’ on Telegram. The applicants were then instructed to download the GrassCall app, which was hosted on a website controlled by the scam group. The website has since been taken offline, but many victims had already been compromised.
Dozens of X and LinkedIn users shared warnings after being targeted by the scam, with job seeker Cristian Ghita posting on Feb. 26 that the scheme was “extremely well-orchestrated”:
“They had a website, LinkedIn and X profiles, and employees listed. It looked legit from almost all angles. Even the video-conferencing tool had an almost believable online presence.”
Fake Identities and Digital Footprints Wiped
Most of the fake job listings have since been removed from LinkedIn and other platforms, but some remain active. A website for Chain Seeker listed a chief financial officer (CFO) named Isabel Olmedo and an HR manager named Adriano Cattaneo, both of whose LinkedIn pages have been erased.
However, an account under the name Artjoms Dzalbs, claiming to be the CEO of Chain Seeker, was still active at the time of writing.
Crypto Users and NFT Traders Are Prime Targets
In its January report, Recorded Future warned that crypto traders, NFT investors, and gaming professionals are at increased risk of being targeted by these scams.
Victims who suspect they have been infected by the GrassCall malware have been advised to immediately use an uninfected device to change all passwords and transfer funds to a new crypto wallet as a precautionary measure.
What’s Next?
As crypto scams become more sophisticated, job seekers and crypto enthusiasts need to be extra vigilant when applying for jobs or downloading unknown applications. The use of social engineering, fake companies, and deceptive recruitment tactics underscores the growing need for heightened security awareness in the crypto space.
With cybercriminal groups like Crazy Evil refining their methods, industry experts anticipate an increase in similar fraudulent schemes, making it crucial for crypto users to verify opportunities before engaging with unknown platforms or individuals.