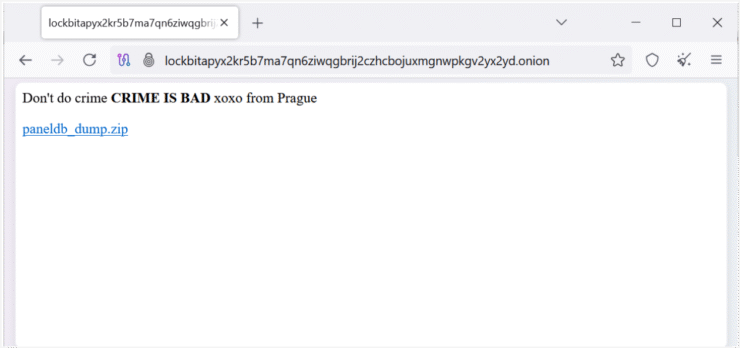
In a striking act of digital retaliation, an unknown group of hackers has breached the affiliate infrastructure of LockBit—a prolific ransomware gang long feared across cyberspace—and publicly leaked nearly 60,000 Bitcoin addresses tied to its operations. The attackers left a cheeky message behind: “Don’t do crime. CRIME IS BAD xoxo from Prague,” delivering a sardonic blow to one of the most notorious cybercrime outfits in the world.
The breach centers around a MySQL database dump—posted online for public access—that included extensive details on LockBit’s ransom payment ecosystem. Among the exposed data are wallet addresses believed to have received ransom payments, build configurations for ransomware variants, and logs of thousands of negotiation chats between LockBit and its victims.
While no private keys were disclosed, cybersecurity experts say the release offers significant intelligence for blockchain investigators and law enforcement. The data could help authorities trace ransom funds, identify intermediaries, and gain new insights into the group’s internal operations.
LockBit has remained one of the most formidable ransomware groups globally, known for targeting critical infrastructure and businesses across multiple continents. The group was previously the subject of a high-profile international crackdown in early 2024, involving cybersecurity agencies from 10 countries. While that effort temporarily disrupted their activities, this latest leak may inflict deeper and more lasting damage.
The event also echoes a similar breach of the Everest ransomware group earlier this year, fueling speculation about a broader wave of counter-cyberattacks aimed at dismantling ransomware syndicates.
No Private Keys Leaked, But Hack Reveals Deep Operational Data
Although nearly 60,000 Bitcoin wallet addresses tied to LockBit’s ransomware campaigns were exposed in the recent breach, no private keys were compromised, according to both cybersecurity analysts and LockBit affiliates. One X user even shared a direct exchange with a LockBit member who acknowledged the breach but insisted that no critical wallet credentials or sensitive data had been lost.
Still, the leak was far from inconsequential. Analysts at Bleeping Computer reported that the dumped MySQL database contained around 20 tables detailing the inner workings of the ransomware operation. Among the most revealing was the “builds” table, listing specific ransomware payloads generated by LockBit affiliates—some of which were tied to known corporate and infrastructure targets.
Also unearthed was a “chats” table containing over 4,400 negotiation records between victims and the ransomware group. These communications offer a rare, detailed view into LockBit’s extortion process—how payment demands were set, how victims responded, and how deals were negotiated. The data provides a trove of actionable intelligence for law enforcement and blockchain forensic teams.
Analysts Link LockBit Breach to Everest Hack
The identity of the hackers behind the LockBit breach remains unknown, but analysts are beginning to draw connections. Experts at Bleeping Computer noted that the message left on LockBit’s defaced portal closely resembles the one used in the recent Everest ransomware group takedown—suggesting a possible link between the two incidents.
While no group has claimed responsibility, the similarity in messaging and tactics points to a potential coordinated campaign targeting high-profile ransomware syndicates. If the LockBit and Everest breaches are indeed connected, it may signal a new chapter in the escalating cyber war between ransomware groups and counter-hacking operatives.
Quick Facts
- Nearly 60,000 Bitcoin addresses associated with LockBit’s ransomware operations were leaked following a breach of the group’s dark web affiliate systems.
- The leaked database includes ransomware payload builds, configuration files, and over 4,400 chat logs from negotiations with victims.
- No private keys were included in the breach, but analysts say the data could help trace illicit payments and uncover organizational structure.
- The hack may be linked to the recent Everest ransomware group takedown, suggesting a possible broader campaign against major ransomware networks.





