A crypto trader lost nearly 98% of their funds in a devastating sandwich attack while swapping stablecoins on March 12, highlighting the ongoing risks of trading on decentralized exchanges (DEXs).
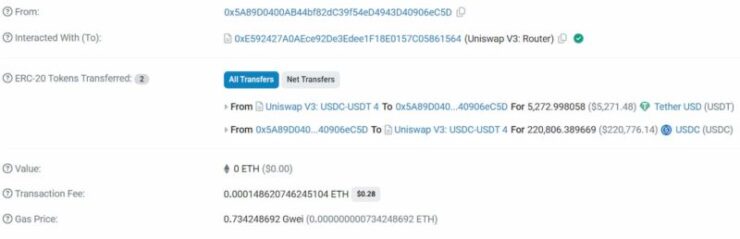
The attack, which exploited Maximum Extractable Value (MEV) tactics, resulted in the trader receiving just $5,271 USDT from an initial $220,764 USDC swap, while the attacker pocketed over $215,500.
The transaction occurred on Uniswap v3’s USDC-USDT liquidity pool, which holds $19.8 million in locked value. According to blockchain data, an MEV bot front-ran the trade by temporarily draining all USDC liquidity from the pool before returning it once the swap was completed.
Michael Nadeau, founder of The DeFi Report, detailed how the attacker manipulated the trade:
- The MEV bot removed all USDC liquidity from the pool, ensuring an unfavorable exchange rate for the trader.
- Once the transaction executed, the bot reinserted the liquidity, reversing the pool’s imbalance.
- The attacker tipped the Ethereum block builder “bob-the-builder.eth” $200,000 and profited $8,000 from the exploit.
Recurring Attacks or Something More?
Blockchain sleuths suspect this was not an isolated incident. DeFi researcher “DeFiac” noted that the same trader—or someone using multiple wallets—has fallen victim to six separate sandwich attacks.
Two additional wallets, “0xDDe…42a6D” and “0x999…1D215”, were targeted minutes earlier, losing $138,838 and $128,003, respectively. All transactions originated from Aave, suggesting funds were borrowed before being swapped on Uniswap.
While some analysts view this as a classic MEV exploitation, others, including DefiLlama founder 0xngmi, speculate that the transactions could be money laundering attempts:
“If you have illicit funds, you could construct a highly MEV-able transaction, privately send it to a bot, and have them arbitrage it within a bundle. That way, you wash the money with almost zero losses.”
Uniswap’s Response and MEV Protection Debate
Initially, critics blamed Uniswap v3 for allowing the attack to occur. However, Uniswap CEO Hayden Adams clarified that the trades did not originate from Uniswap’s front-end, which has built-in MEV protection and default slippage settings to prevent sandwich attacks.
Michael Nadeau, who had initially pointed fingers at Uniswap, later retracted his criticisms, acknowledging that the attack exploited external execution routes rather than Uniswap’s native platform.
What This Means for DeFi Traders
This attack underscores the vulnerabilities of trading on decentralized exchanges, particularly for traders who lack proper slippage settings or MEV protection.
- MEV bots continue to extract millions from unsuspecting traders using automated arbitrage and front-running techniques.
- Traders using DEX aggregators or non-protected routes remain highly vulnerable.
- DeFi platforms are racing to implement stronger anti-MEV protections, but these measures are not foolproof.
To minimize the risk of MEV exploits, traders should:
- Use MEV-protected platforms like Uniswap’s official front end.
- Set slippage limits to avoid excessive price swings.
- Monitor on-chain liquidity before making large swaps.
- Split transactions into smaller amounts to reduce bot visibility.
Final Thoughts
The $215K sandwich attack on Uniswap v3 is a stark reminder of the hidden dangers of DeFi trading. While Ethereum’s MEV economy fuels liquidity and price efficiency, it also enables ruthless exploitation of unsuspecting traders.
Until stronger protections are implemented, traders must remain vigilant or risk becoming the next victim of DeFi’s dark side.