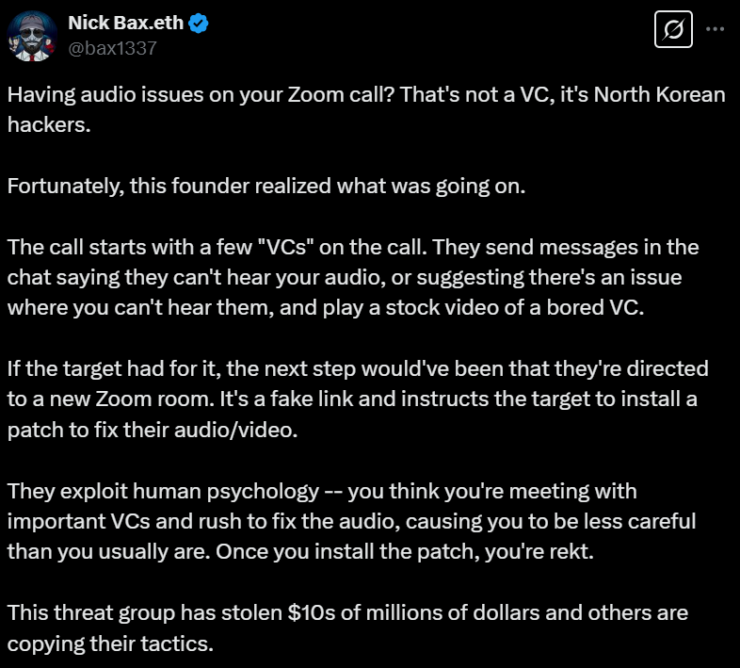
A new wave of North Korean-linked cyber attacks is targeting crypto founders, using fake Zoom calls to deploy malware and steal sensitive data. At least three crypto executives have reported encountering the scam, which exploits human psychology to trick victims into installing malicious software.
According to Nick Bax, a member of the white hat hacking group Security Alliance, the attackers pose as venture capitalists (VCs) or potential partners. The scam unfolds in the following steps:
- The victim is invited to a Zoom meeting or another virtual call under the pretense of a business opportunity.
- Once the call starts, the attackers claim to be experiencing audio issues, displaying a stock video of a VC appearing disengaged.
- They then send a fake link, instructing the victim to install a patch to fix the audio or video problem.
- Once installed, the malware infects the victim’s device, granting the hackers access to critical data, including private keys and login credentials.
Crypto Founders Sound the Alarm
The attack has been attempted on several crypto executives, including:
- Giulio Xiloyannis, co-founder of Mon Protocol, who was nearly duped into installing malware after being asked to switch to a different Zoom link.
- David Zhang, co-founder of Stably, who noted the scam attempted to mimic a normal Zoom interface but wasn’t optimized for mobile devices.
- Melbin Thomas, founder of Devdock AI, who disconnected his laptop after realizing the deception but remains concerned about lingering risks.
A Growing Cyber Threat from North Korea
These attacks come on the heels of a January 14 warning from the U.S., Japan, and South Korea, highlighting the rising danger of North Korean crypto hackers. The notorious Lazarus Group, responsible for some of the biggest cyber heists in Web3, is suspected to be behind many of these operations.
Recent attacks linked to Lazarus Group include:
- The $1.4 billion Bybit hack.
- The $600 million Ronin network exploit.
- Most recently, the continuous laundering of stolen funds using crypto mixers like Tornado Cash resulted in a 400 ETH ($750,000) transaction detected by blockchain security firm CertiK.
With social engineering attacks on the rise, crypto professionals must take extra precautions:
- Verify meeting links — Always cross-check URLs before joining calls.
- Avoid installing software from unverified sources — Legitimate Zoom updates come only from the official site.
- Use a separate, secure device for calls — Consider keeping work and crypto-related activities on different machines.
- Enable hardware security keys — Protect sensitive accounts with multi-factor authentication.
Final Thoughts
The crypto industry must remain vigilant as North Korean hackers refine their tactics. These fake Zoom attacks demonstrate the increasing sophistication of cybercriminals, blending social engineering with technical exploits to target high-value individuals in Web3.
With billions in stolen assets, North Korea’s cyber units continue to pose one of the biggest threats to the digital asset space. Crypto founders and investors must stay informed and implement strict security measures to protect themselves from these ever-evolving attacks.





