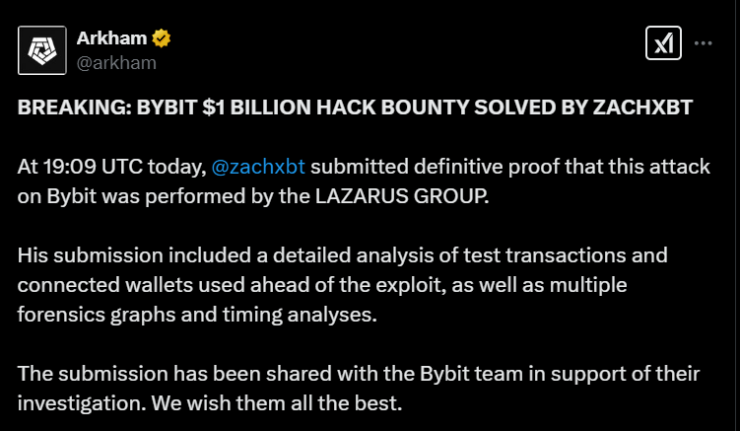
The massive $1.5 billion hack on Bybit has officially been attributed to North Korea’s notorious Lazarus Group, following a thorough investigation by Arkham Intelligence. The confirmation came after renowned blockchain investigator ZachXBT submitted decisive evidence pinpointing Lazarus as the perpetrators behind what is now considered the largest single theft in crypto history.
At exactly 19:09 UTC on Friday, ZachXBT presented Arkham with a comprehensive analysis detailing the attack. His report included forensic breakdowns of test transactions, a web of connected wallets used during the exploit, and in-depth timing analyses that traced the hack’s execution. Arkham shared this critical information with Bybit’s internal team, aiding their ongoing investigation into the breach.
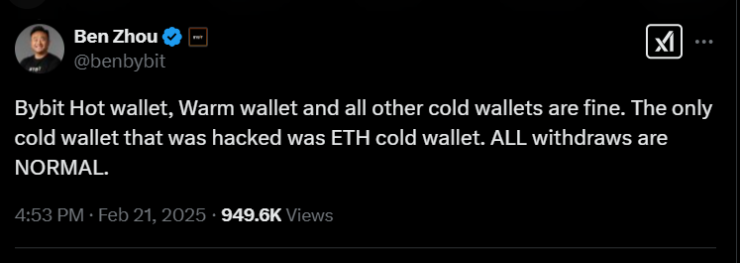
Earlier that day, Bybit confirmed the devastating security lapse, acknowledging the loss of over $1.5 billion in crypto assets. Co-founder and CEO Ben Zhou assured users that all client withdrawals would still be processed, though some may undergo additional scrutiny to ensure the platform’s stability and security.
In an effort to expedite the hunt for the culprits, Arkham announced a bounty of 50,000 ARKM tokens—worth approximately $32,000—for any investigator who could crack the case. Thanks to ZachXBT’s swift detective work, the bounty was quickly claimed, further cementing his reputation as one of the most effective on-chain sleuths in the industry.
The Bybit Breach: Unpacking the Attack
The Bybit hack, now ranked among the largest in crypto history, revealed a sophisticated manipulation of the exchange’s security layers. Hackers managed to siphon off over $1.4 billion in Ethereum from Bybit’s multisig cold wallet, exploiting a routine transfer to the platform’s warm wallet and deceiving internal security protocols.
According to Bybit’s co-founder and CEO, Ben Zhou, the breach stemmed from a cleverly masked transaction. Zhou explained that while initiating a standard transfer from the cold wallet, signers were presented with a manipulated user interface that appeared legitimate. This fake interface displayed the correct destination address and was routed through what seemed like a secure Safe URL. However, hidden beneath the surface was a malicious signing message that altered the smart contract logic of the cold wallet. Once the signers unknowingly approved the altered contract, the hackers gained full control, allowing them to sweep the wallet clean.
The attackers then initiated a complex laundering process. The stolen Ethereum was initially funneled into an address starting with 0x476, which alone received over 400,000 ETH—worth around $1.1 billion—alongside 90,000 stETH, 15,000 cmETH, and 8,000 cETH. Utilizing the “sweep ETH” function, a smart contract mechanism designed to transfer all tokens from one contract to another, the hackers efficiently emptied the cold wallet into their possession.
But the operation didn’t stop there. To obscure the trail, the funds were swiftly divided across three primary distribution wallets—0xB4a, 0x23Ob, and 0x83Ef5. These addresses further broke down the assets, distributing them into dozens of newly generated wallets. The hackers then began swapping the stolen funds using major decentralized exchanges like Uniswap, Paraswap, and KyberSwap. Even the liquid staking tokens, such as stETH, were exchanged for ETH, a move that some security experts suggest was intended to reduce the risk of asset freezing.
By Friday evening, Arkham Research reported that the original 0x476 wallet, once holding over $1 billion, had been drained to just $3.7 million, underscoring the speed and efficiency of the laundering process.
A Pattern of Cyber Assaults: Lazarus Group’s Ongoing Campaign
This attack on Bybit is not an isolated event. The Lazarus Group has a well-documented history of targeting cryptocurrency platforms to amass funds for North Korea. In 2024 alone, they were responsible for multiple heists totaling over $650 million, including a $235 million theft from India’s WazirX exchange and a $308 million breach of Japan’s DMM Bitcoin, which led to the exchange’s closure.
Their modus operandi often involves sophisticated social engineering tactics, such as impersonating recruiters on professional networks to infiltrate organizations.
Quick Facts:
- Bybit suffered a $1.5 billion Ethereum theft during a routine wallet transfer.
- The hack has been attributed to North Korea’s Lazarus Group.
- In 2024, Lazarus was linked to multiple crypto heists exceeding $650 million.





