BnB network-based Four.meme coin launchpad suffered a security breach in the early hours of the day on March 18, resulting in the loss of more than 300 BnB worth of liquidity.
The latest attack on Four.Meme marks the second major exploit the launchpad has suffered in the past two months, once again exposing vulnerabilities in its smart contract architecture. According to blockchain security firm SlowMist, the exploit was carried out on Tuesday morning, specifically targeting a critical flaw in Four.Meme’s liquidity mechanism.
The attacker reportedly leveraged this flaw to bypass transfer restrictions and manipulate liquidity pool pricing, allowing them to drain substantial funds from the project’s token liquidity pool on PancakeSwap. Smart contract audit firm QuillAudits further confirmed that the breach stemmed from weaknesses in how liquidity was managed within the platform’s code.
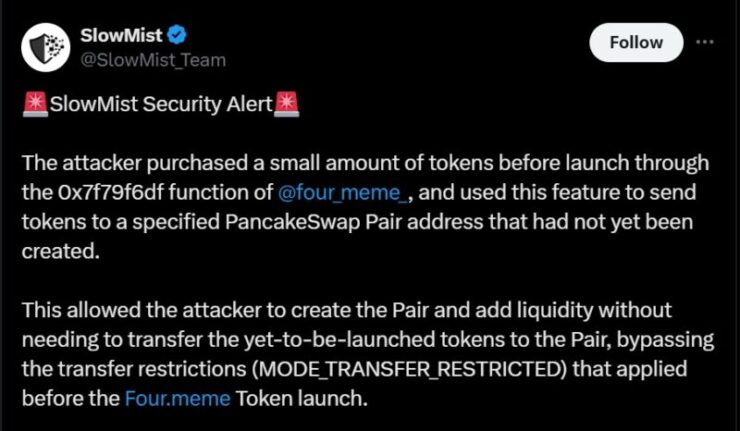
This follows an earlier attack on Four.Meme, which occurred two months prior, where a separate vulnerability led to the loss of $183,000. That exploit similarly involved liquidity manipulation on PancakeSwap, although it exploited a different flaw in the platform’s contract logic.
How the Hack was Accomplished
Further investigation into the exploit has revealed how the attacker strategically moved and laundered the stolen funds to cover their tracks. Blockchain analysis shows that days before the attack, the hacker withdrew approximately 69 BNB from a FixedFloat hot wallet (0x47…c95), setting the stage for the exploit.
During the attack, the malicious actor deployed multiple smart contracts to execute the exploit and siphon funds. After successfully draining liquidity, the hacker funneled around 67.3 BNB into one wallet address (0x4c…805) and transferred an additional 205 BNB to another wallet (0x88…456). From there, the 205 BNB was fragmented and distributed across four separate wallets in an attempt to obscure the fund flow.
To further launder the stolen assets, the hacker utilized PancakeSwap’s $BROCCOLLI 3 contract, swapping approximately 192 WBNB and redistributing the proceeds across various PancakeSwap liquidity pools, including contracts labeled DCA 32 (0x77C1dF8…), MuBroccoli (0xcaC54d89…), and others.
These laundering tactics reflect a common strategy among DeFi exploiters, who often exploit the relative anonymity and liquidity of decentralized exchanges to evade detection and complicate recovery efforts. Despite the sophisticated maneuvering, on-chain analysts continue to trace the transactions in hopes of identifying potential leads.
Four.Meme Responds, Promises User Compensation
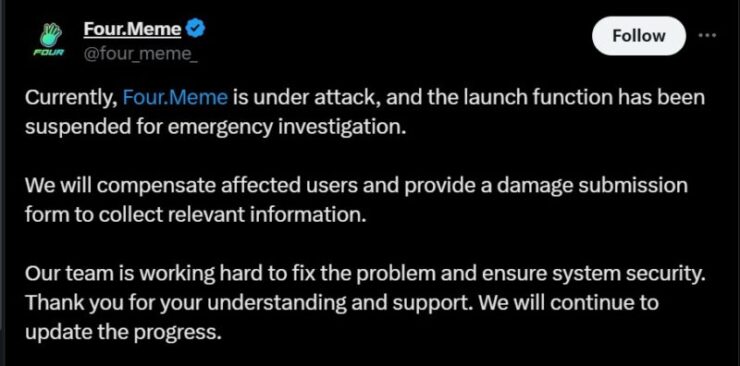
In the wake of the exploit, Four.Meme moved quickly to halt operations, suspending its token launch function to prevent further damage. Shortly after confirming the breach, the platform issued an emergency statement, assuring users that affected parties would be compensated.
The team announced plans to distribute a damage submission form to collect claims and relevant information from impacted users. A few hours later, Four.Meme revealed that it had resumed normal operations following an internal security audit, stating that additional safeguards had been implemented to strengthen the platform’s infrastructure.
Since its inception, Four.Meme has experienced rapid growth, with data from Dune Analytics showing over 74,600 unique tokens launched on the platform to date. As the meme coin market heats up, the rapid proliferation of new tokens has also attracted bad actors eager to exploit hastily built smart contracts and liquidity structures. Vulnerabilities in permission settings, liquidity pools, and tokenomics are frequent attack vectors, putting both developers and investors at risk.
Quick Facts:
- Four.Meme suffered its second exploit in two months, with attackers draining over 300 BnB.
- The latest attack targeted a critical flaw in Four.Meme’s liquidity mechanism, allowing manipulation of liquidity pool pricing.
- A previous exploit in the platform two months earlier resulted in a $183,000 loss due to a different vulnerability.
- Four.Meme initially suspended operations temporarily and pledged to compensate affected users after conducting security audits.





