Decentralized exchange aggregator 1inch has confirmed a $5 million hack, caused by a smart contract vulnerability in its outdated Fusion v1 implementation. While user funds remain secure, the incident raises serious concerns about DeFi security and the importance of regular contract audits.
The breach was first identified on March 5, when 1inch detected a vulnerability in Fusion v1 resolvers the entities responsible for filling trades. The exploit was made public a day later, prompting immediate security reviews.
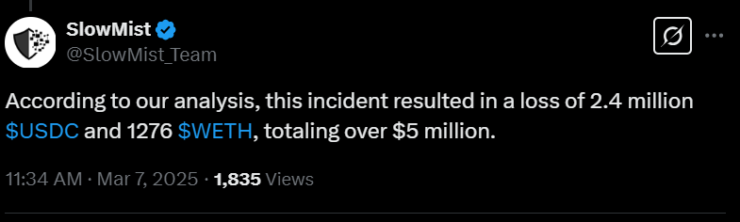
On March 7, blockchain security firm SlowMist conducted an on-chain investigation, revealing that the attacker managed to siphon:
- 2.4 million USDC
- 1,276 Wrapped Ether (WETH)
1inch confirmed that only outdated Fusion v1 resolvers were affected, reassuring users that their funds remained safe.
1inch Responds With Urgent Security Measures
Following the breach, 1inch urged all resolvers to audit and update their contracts immediately, stating:
“We’re actively working with affected resolvers to secure their systems. We urge all resolvers to audit and update their contracts immediately.”
To prevent future attacks, 1inch has:
- Launched a bug bounty program to identify and mitigate potential vulnerabilities.
- Collaborated with affected resolvers to enhance their security frameworks.
- Explored fund recovery options, though chances of reclaiming stolen assets remain low.
Historically, recovery efforts in crypto hacks have been mixed. While some hackers agree to return funds in exchange for a 10% whitehat bounty, others vanish without a trace.
For instance:
- Crypto lender Shezmu successfully negotiated the return of most stolen funds, offering a 10% bounty to the hacker.
- Bybit’s $1.5 billion hack—the largest crypto heist ever—saw attackers siphon the entire amount, despite coordinated recovery efforts.
Given this precedent, 1inch’s chances of retrieving the stolen $5 million are uncertain, unless the hacker voluntarily agrees to return the funds.
How the Bybit Hack Highlights a Major Risk
While 1inch lost $5 million, the recent Bybit hack which saw $1.4 billion drained, illustrates just how devastating security lapses in DeFi protocols can be.
- Bybit was forced to take emergency loans to ensure seamless withdrawals for users.
- Hackers laundered the stolen funds in just 10 days, using crosschain swaps and mixing protocols to obscure their trail.
- THORChain, a crosschain swap protocol, saw a surge in activity, as the attackers used it extensively to move funds.
What’s Next for 1inch?
The 1inch team has pledged to reinforce its security measures, urging:
- Resolvers to migrate to the latest Fusion contracts.
- Stronger onchain monitoring to detect anomalies faster.
- Collaboration with security firms to prevent future exploits.
As DeFi protocols continue to evolve, regular security audits and proactive updates will be critical in preventing exploits like the 1inch Fusion v1 attack.
The 1inch hack serves as another reminder that even well-established DeFi platforms are not immune to vulnerabilities, making security a top priority in the future of decentralized finance.





