A sophisticated hack on the decentralized finance protocol SIR.trading has drained $355,000—its entire total value locked—exposing a potential vulnerability in Ethereum’s transient storage feature introduced in the Dencun hard fork.
The March 30 exploit was first flagged on social media by security firms TenArmorAlert and Decurity.
“Our system has detected a suspicious attack involving #SIR.trading… resulting in an approximate loss of $353.8K,”
TenArmorAlert posted on X. Decurity confirmed the breach, citing the protocol’s Vault contract and describing the incident as a “clever attack.”
The vulnerability centered on the Vault contract’s uniswapV3SwapCallback function, which relied on transient storage to verify the caller’s address. According to Decurity, the function initially checks the message sender against a stored Uniswap pool address. However, at the end of execution, it overwrites that same storage slot with a value known as amount, which can be manipulated externally.
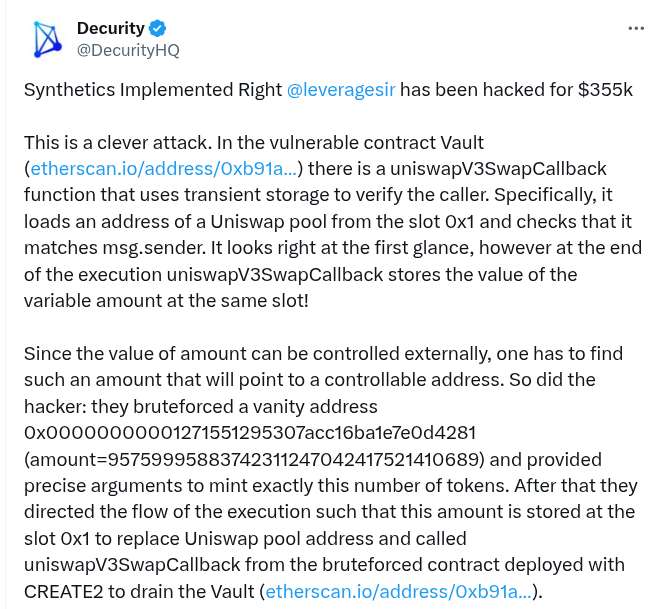
Using a brute-force technique, the attacker generated a vanity address and crafted a precise amount value—95759995883742311247042417521410689—that corresponded to their contract address. This allowed them to overwrite the legitimate Uniswap pool address and redirect the callback function to their deployed contract, draining the Vault.
Experts Warn of Deeper Smart Contract Risks
Supremacy’s Yi described the hack as “gas-optimized evil,” emphasizing how the attacker exploited a low-cost feature with significant execution risk. “This exploit highlights transient storage’s Achilles’ heel: its low gas cost… makes it attractive, but it’s cleared only at tx end,” Yi wrote. He noted that this feature, while cost-effective, creates new vectors for reentrancy if used improperly.
The attacker leveraged Ethereum’s CREATE2 opcode to deploy a contract to the brute-forced vanity address, allowing for seamless redirection of the callback execution. This demonstrated a high level of technical precision in both contract design and execution.
Blockchain researcher Yi from Supremacy provided further technical analysis on X. “The hacker’s brilliance: they bruteforced a vanity address… called hook from this contract to drain the Vault. Pure gas-optimized evil,” Yi wrote. He emphasized the broader implication of the attack, noting that “transient storage isn’t as ‘transient’ as you’d think.”
Transient storage, introduced in Ethereum’s Dencun upgrade, allows for temporary data storage with reduced gas costs compared to traditional methods. However, as Yi highlighted, the storage only clears at the end of a transaction, making mid-execution writes susceptible to reentrancy and manipulation.
“This isn’t merely a threat aimed at a single instance of uniswapV3SwapCallback,” Yi warned. Decurity echoed that the design flaw lies in how transient storage interacts with critical logic inside callback functions.
The stolen funds have reportedly been moved into Railgun, a privacy-focused Ethereum solution. TenArmorAlert confirmed the transfer, and SIR.trading’s founder, known as Xatarrer, has since reached out to Railgun for assistance.
SIR.trading, short for Synthetics Implemented Right, had marketed itself as “a new DeFi protocol for safer leverage,” aimed at reducing volatility decay and liquidation risk. The protocol had previously warned that its smart contracts, despite audits, could still harbor critical bugs, particularly in its vault logic.
Security researchers say this breach may mark one of the first real-world attacks exploiting Ethereum’s transient storage.





