The decentralized lending protocol Abracadabra Finance has become the latest victim in a wave of DeFi exploits, suffering an estimated $13 million loss in ETH due to a targeted vulnerability in its smart contract integration with GMX liquidity tokens.
According to blockchain security firm PeckShield, the incident occurred on March 25 and involved a sophisticated breach of the platform’s “cauldrons” — lending modules that allow users to borrow assets against crypto collateral. Specifically, the attack targeted cauldrons connected to GMX V2 liquidity pools, a feature that was meant to provide decentralized and efficient on-chain borrowing.
Security researchers suggest the exploit hinged on manipulating the liquidation logic tied to these cauldrons. By tampering with the way positions were managed within the GMX integration, the attacker successfully drained 6,260 ETH — approximately $13 million — from Abracadabra’s protocol.
GMX, the decentralized exchange that offers perpetual futures and spot trading, has clarified that its own contracts were not compromised. The vulnerability was isolated to the way Abracadabra’s smart contracts used GM tokens; tokenized representations of GMX liquidity positions — as collateral within its lending infrastructure.
Abracadabra Confirms Exploit, Offers Attacker 20% Bounty
Abracadabra Finance has officially acknowledged the exploit, confirming the incident in a statement shared via X. The protocol said its core engineers, alongside external partners, are actively investigating how the attacker was able to bypass security safeguards within a contract that had previously passed third-party audits.
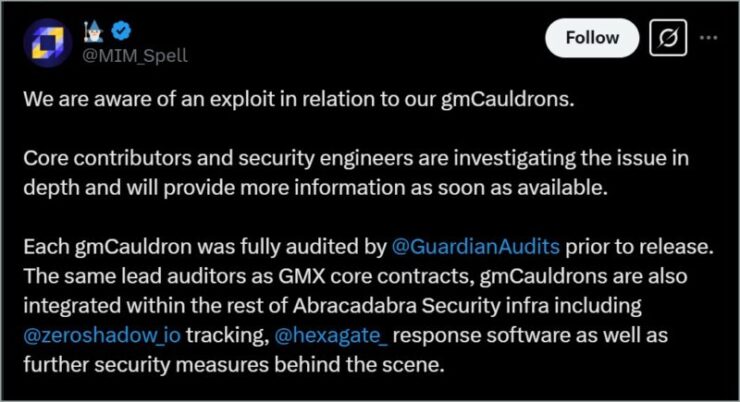
The exploit targeted a smart contract referred to as a “gmCauldron,” which allows users to borrow against GMX liquidity tokens. While the cauldron had been audited by Guardian Audits, the same firm responsible for reviewing GMX’s own contracts, Abracadabra noted that the vulnerability had escaped initial detection.
The platform emphasized that these contracts were part of a larger ecosystem fortified by real-time monitoring and response tools, none of which were sufficient to halt the breach in progress.
“While having multiple systems in place, the exploit was caught only after the attacker executed several transactions. The Zeroshadow team alerted us and we quickly turned off all borrows to all cauldrons.” The confirmation post stated.
In an unusual but increasingly common response, Abracadabra extended a 20% white-hat bug bounty to the attacker, urging them to return the stolen funds and open a dialogue via email or an on-chain message. This method, often used in DeFi circles, seeks to incentivize ethical resolution without resorting to legal pursuit.
The protocol is now coordinating closely with GMX, Guardian Audits, and other DeFi security experts to determine the technical details of the exploit and prevent future recurrence. A full post-mortem has been promised once the internal review is complete.
Notably, Abracadabra also reassured its users that no individual collateral deposits were affected during the breach, limiting the impact strictly to protocol liquidity.
While the specific method of this exploit is still under investigation, it bears similarities to flash loan attacks—a prevalent threat in the DeFi space. Flash loans allow users to borrow substantial amounts without collateral, provided the loan is repaid within the same transaction. Malicious actors can exploit this mechanism to manipulate market prices or exploit vulnerabilities in smart contracts.
The stolen funds have since been bridged from Arbitrum network to Ethereum mainnet. In January 2024, Abracadabra’s MIM stablecoin was manipulated leading to a $6 million worth of losses.
Quick Facts:
- Abracadabra Finance was exploited for 6,260 ETH (approx. $13M) on March 25.
- The attacker targeted cauldrons using GMX liquidity tokens as collateral.
- GMX confirmed its smart contracts were not compromised; the issue was isolated to Abracadabra’s integration.