A new strain of cryptojacking malware, dubbed MassJacker, has been identified as a growing threat to cryptocurrency users.
This malicious software targets individuals seeking pirated content, stealthily hijacking crypto transactions by swapping stored wallet addresses with those controlled by attackers.
The malware, first reported by CyberArk on March 10, brings to light the increasing risks associated with downloading unauthorized software.
The MassJacker malware originates from the website Pesktop[.]com, which lures users under the pretense of offering free access to paid software. Unbeknownst to users, attempting to download files from this site results in installing hidden malware on their systems. Once the malware is embedded, it monitors the victim’s activity, specifically targeting clipboard data used for cryptocurrency transactions.
MassJacker detects when a user copies a crypto wallet address—a common step when making digital asset transfers. Instead of allowing the user’s original address to remain in the clipboard, the malware replaces it with a wallet address belonging to the attacker, redirecting funds without the victim’s knowledge. This deceptive attack method, commonly called a “clipper” attack, is particularly effective because users often fail to double-check wallet addresses before executing transactions.
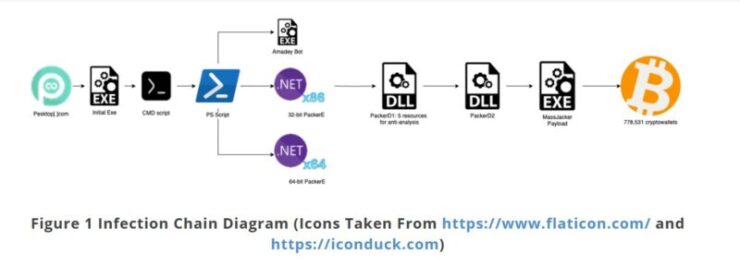
MassJacker’s Reach and Financial Impact
CyberArk’s analysis of the malware operation revealed that it is linked to at least 778,531 unique wallet addresses, suggesting a large-scale, coordinated cybercrime effort. However, only 423 wallets actively held crypto assets at the time of investigation.
The total estimated value of stolen cryptocurrency linked to these wallets reached $336,700 as of August 2024. A particularly active wallet tied to the operation contained over 600 Solana (SOL), valued at approximately $87,000. Investigators also discovered a history of decentralized finance (DeFi) transactions within this wallet, including token swaps involving Jupiter (JUP), Uniswap (UNI), USDC, and Raydium (RAY), indicating that attackers were laundering stolen funds through various DeFi platforms.
MassJacker employs stealth techniques to avoid detection unlike traditional phishing or ransomware attacks. The malware does not demand ransoms or alert victims to its presence, making it difficult to identify. Instead, it works discreetly in the background, allowing attackers to siphon funds over time.
MassJacker also utilizes anti-debugging features and Just-In-Time (JIT) hooking to prevent security researchers from analyzing its source code. These tactics allow it to bypass antivirus software and remain hidden within infected systems for extended periods.
The Evolving Threat of Crypto Malware
MassJacker is part of a broader trend of crypto-targeting malware that has evolved significantly in recent years. Since the early days of Coinhive’s cryptojacking scripts in 2017, cybercriminals have continuously developed more sophisticated ways to exploit unsuspecting users. Recent reports from cybersecurity firms have flagged multiple new attack methods, including:
- Fake job recruitment scams that trick victims into installing malware under the guise of fixing technical issues during video interviews.
- Malicious Python Package Index (PyPI) libraries that inject crypto-stealing malware into developer environments.
- Mobile malware hidden within app development kits that scan screenshots for crypto seed phrases.
Hackers are becoming increasingly creative in their methods as the cryptocurrency market expands, making vigilance and cybersecurity best practices crucial for users who store and transact digital assets.
Quick Facts:
- MassJacker is a newly discovered cryptojacking malware that targets users downloading pirated software.
- Malware hijacks their crypto transactions by replacing wallet addresses on the clipboard.
- The malware originates from Pesktop[.]com, a piracy site that covertly installs malicious software, allowing attackers to steal digital assets.
- CyberArk identified over 778,531 unique wallet addresses tied to the operation, with at least $336,700 in stolen funds.
- MassJacker employs stealthy evasion techniques, using anti-debugging tools and JIT hooking to avoid detection by antivirus programs.





